Navigation
Overview Top
VPN or Virtual Private Network is a network that connects a user's computer or device (client) to a server in a secure manner. This provides the user an experience that they would have only when being inside the network from anywhere in the world.
VPN can be implemented either by special client-side software or by special hardware-based solution. Hardware-based solutions are typically expensive, require extensive configuration and limit where a user can connect from.
Software-based VPN solutions are more popular among people who frequently travel and would want to connect to their workplace or any server securely. The software-based VPN solutions are installed on the user's computers or devices and provide immediate connectivity to the servers they need to connect to.
StealthWalker is a software-based VPN tool. It provides easy connectivity for the user and has a very straightforward mechanism to establish a VPN connection.
The following features make StealthWalker the best if not unique:
- Multiple layers of encryption including DNS encryption and protection against DNS leaks.
- Fast VPN servers and bandwidth misuse monitor to avoid bottlenecks and overload issues.
- Custom Tor-enabled built-in browser to offer multiple encryption layers, improved privacy and anonymity.
- All-in-one built-in privacy solution offered by third-party open source tools.
- Custom control panel for Enterprise clients with advanced features such as user management & control, VPN server management and more.
- Reliable and affordable high-speed VPN services with variety of subscription plans.
How StealthWalker Works
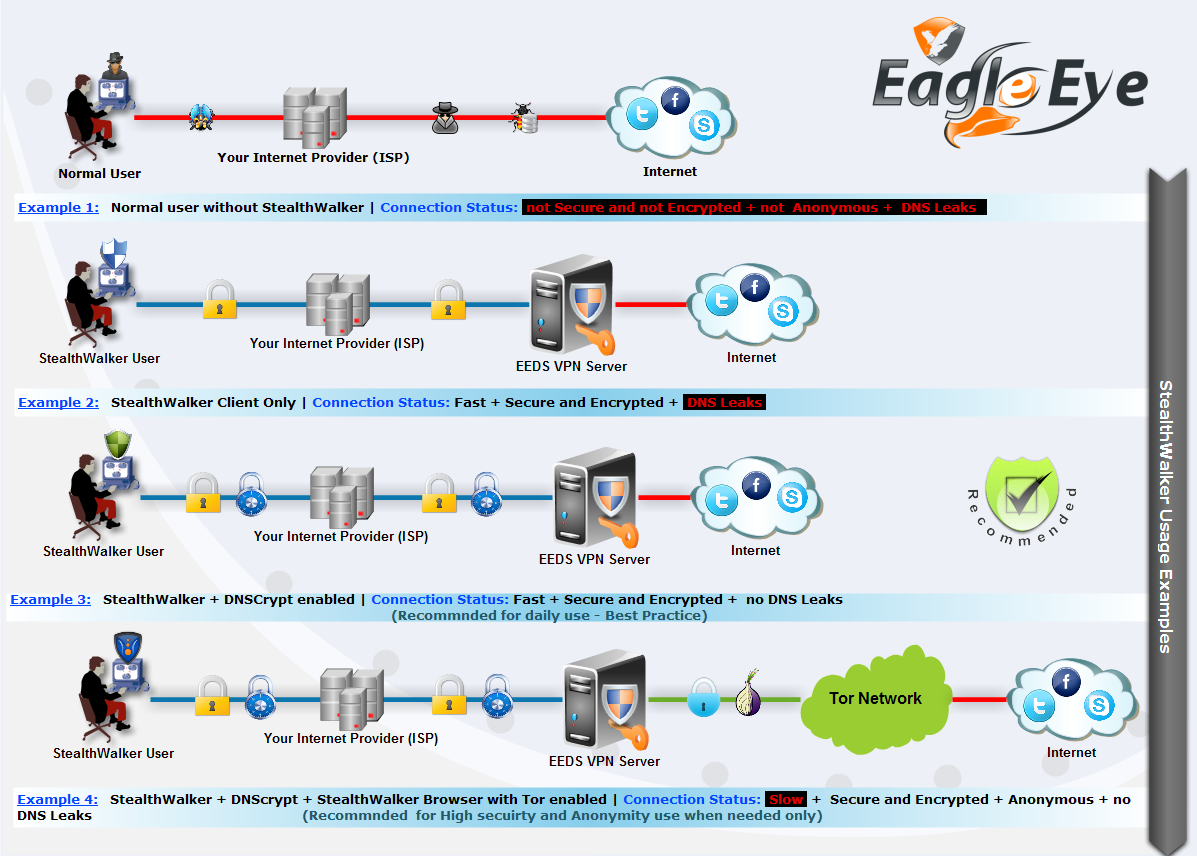
Getting Started Top
Key Features
StealthWalker is a software-based VPN tool. It provides easy connectivity for the user and has a very straightforward mechanism to establish a VPN connection. StealthWalker creates an encrypted tunnel between your PC and the server, which means not only your browsing is secure, but also all communication going through the Internet, such as MSN, Skype, FTP, Email, etc. are encrypted.
StealthWalker has been developed by Eagle Eye Digital Solutions (EEDS), a professional IT security service provider, specializing in the growing markets of computer, mobile and Internet forensics as well as software and website development.
These features can be very useful in situations like:
- Browsing Internet securely using public Access Points and WiFi hotspots.
- Hiding your real identity online while using Forums, Blogs and Social networks.
- Encrypting (AES-256) and hiding your Internet traffic from ISP or local network attackers.
- Enhanced user's guide.
- Enhanced user management system (click here to view).
StealthWalker allows you to connect to one of the secure servers hosted by EEDS. It assigns an IP address from that network and allows you to get on to the Internet without revealing your identity or location. When connected to the secure servers using StealthWalker, all communication over the Internet is encrypted.
System Requirements
PC running Microsoft Windows® operating system:
- Microsoft Windows 2000® with Service Pack 4
- Microsoft Windows XP® with Service Pack 2 or greater
- Microsoft Windows Vista® 32/64 bit
- Microsoft Windows 7® 2003 32/64 bit
- Microsoft Windows 8®
Some third-party applications bundled with StealthWalker, like Keepass, may require .NET framework to be installed to run correctly.
Installation
StealthWalker has a very straightforward installation process. Once you have purchased the software, you can register yourself to create a username and password. Once activated, this information will authenticate you to the servers.
You can download the software from https://www.digi77.com/software/vpn/update/StealthWalker-Setup.exe.
Click on "StealthWalker-Setup.exe" file to start the installation. If you already have a version of StealthWalker installed, you will be asked if you want to remove the previous version and install the current one. Follow the instructions on the screen to choose the location of installation and other information.
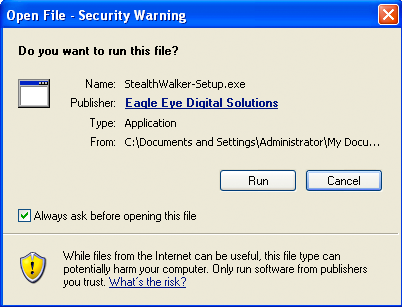
You may be prompted with a warning when running this file as shown below. This digital certificate is to ensure that the installation files have not been altered and is signed by EEDS. It is safe to run the installer.
The next step will prompt you to choose the components you want to install.
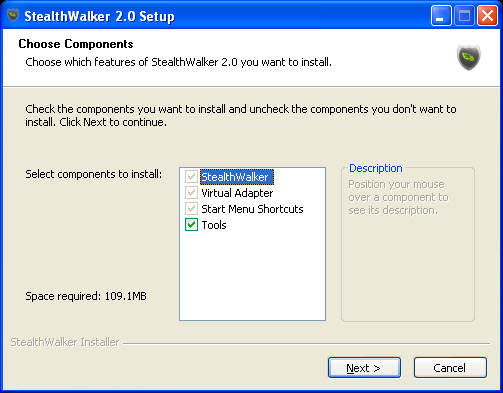
- StealthWalker: main program file and needs to be installed.
- Virtual Adapter: software driver used to establish VPN connections.
- Start Menu Shortcuts: creates shortcuts for StealthWalker on the Windows "Start" menu and the desktop.
- Tools: additional programs packaged with StealthWalker that provide various system utilities. It is recommended not to uncheck the tools to ensure that StealthBrowser and all 3rd part security tools are properly installed.
Then you will be prompted to choose where you want to install the program at.
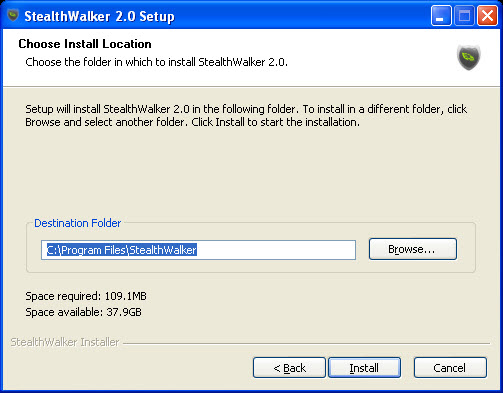
It will then copy all necessary files and complete the installation.
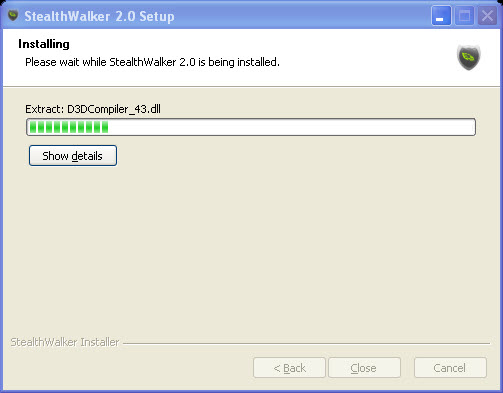
When the drivers for the VirtualAdapter are installed, you may be given a warning. It is safe to continue the installation. Click on "Continue Anyway".
Once all files are copied, the installer will provide a confirmation that the installation is complete. Click on to end the installation process.
Run the StealthWalker application by clicking (or double-clicking) on the application shortcut. You will be shown the main screen.
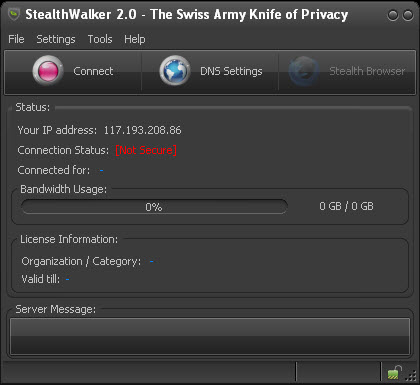
If you see this screen, it indicates that the StealthWalker installation is complete and you are ready to use the software to establish VPN connections.
Once your account is activated, your can log in to the VPN software after installation using the username and password that you create during registration.
Note: You will need to have an active internet connection to be able to log in to the software.
User Interface / Using StealthWalker Top
Main Window
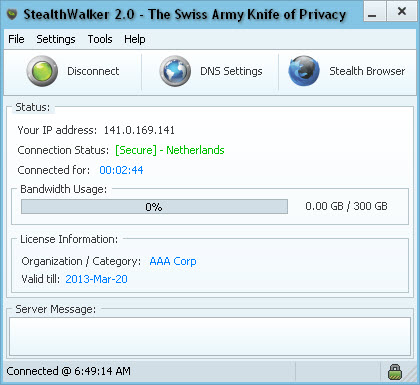
Once logged in, StealthWalker has a very simple and straight-forward user interface.
The StealthWalker software is basically one application window. It has a set of navigation menus on the top. These provide connection logs, software options, add-on tools and help information.
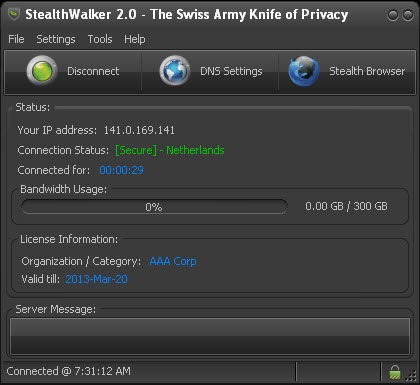
The center area contains the Status panel that shows the active connection information, your license information and provides most of the interface for the functionality of StealthWalker.
The footer consists of the status bar that displays the status of the VPN connection.
Registration
You can register for a free account by clicking on the button and then clicking on the button. This will bring up the registration box as shown below.
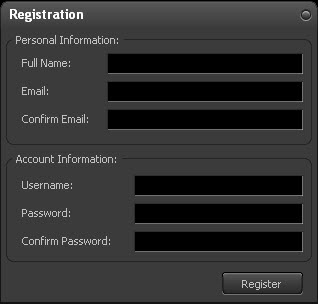
You have to fill in your Full Name, Email (typed twice for confirmation), your chosen Username and Password (typed twice for confirmation). Then clicking on the button creates a 30-day trial account for you. An email is sent to you for activation. Correct email information is important without which you will not be able to activate your account.
Once you have paid for the license, this account will be activated and will be available for the purchased period.
Connecting and Disconnecting
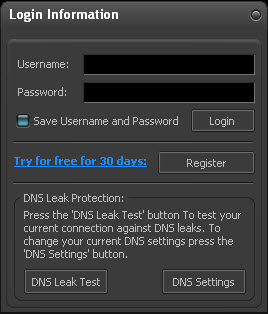
To connect to the dedicated VPN servers, you will need to click on the button.
You will be prompted to log in using the supplied Username and Password. Type your username and password (assigned to you by your administrator) and click on the button.
You also have the option of trying StealthWalker free for 30 days by registering online.
As the connection is established, you will be able to see the progress in the status bar. StealthWalker will first send your login information to the EEDS servers, then establish a VPN connection and then assign your computer an IP address on that network.
If the connection is successfully established, you will see a "Connected" message on the status bar. The red button will also now change to a green button. You will also get a notification on the system tray area.
The screen will now provide you information on what your new IP address is, which server you have been connected to, your organization and the validity of your account. It also shows how much of your allocated bandwidth has been used. Once it crosses 90% usage, it will start to blink to alert you. You will also see a lock icon at the bottom-right corner of the StealthWalker application.

To disconnect the VPN connection, click on the "Disconnect" button. To exit StealthWalker, click on the last button (which changes to red as you hover your mouse over it) on top of the application or choose from the menu.
DNS Settings
The button allows you to configure your DNS options. Domain Name Services (DNS) resolve the website addresses that you type on your browser(s) and direct you to them.
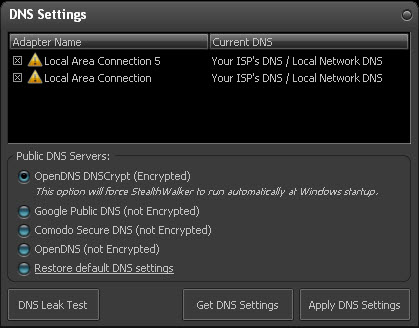
It lists the different network adaptors that you have and what DNS they use. You also have the option of trying out different publicly available DNS like OpenDNS DNSCrypt, Google Public DNS, etc. At any point of time, you can restore you default DNS by selecting the "Restore default DNS settings" option.
To use the selected DNS, click on .
The default option is OpenDNS DNSCrypt. DNSCrypt secures all communication from your computer to the OpenDNS servers by encrypting them. This prevents and secures your communication from eavesdropping or man-in-the-middle attacks. This is highly recommended to protect your privacy and online security while using StealthWalker.
You also have the option of testing for DNS leaks from within StealthWalker. DNS leaks occur when all private or anonymous traffic is not routed through the anonymity network. Some traffic is routed through your regular network and hence can be monitored by the network provider. Hence this is called a "leak".
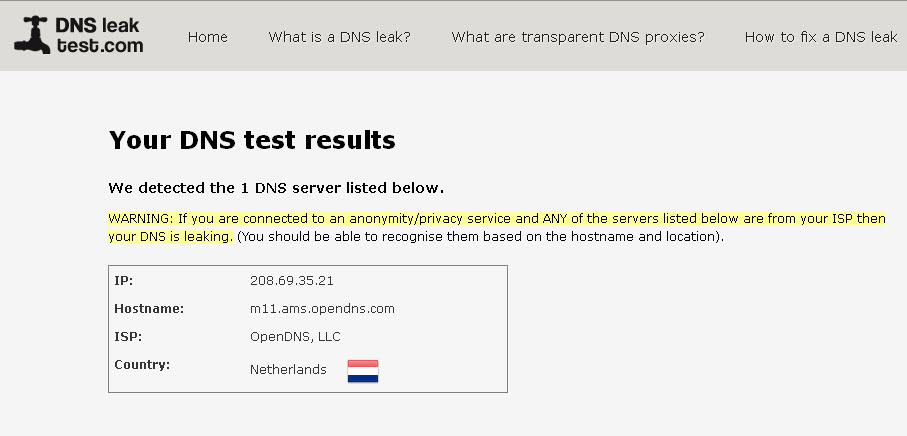
StealthWalker uses an online service at www.dnsleaktest.com to check for DNS leaks. The service determines your DNS and provides information on your IP, Host name, Region, among others. If you see the regular host name or region in that list while your StealthWalker connection is active, then you know that DNS leak is occurring.
Main Menu
The following are the menu items available in StealthWalker:
File
The menu has two items - and .
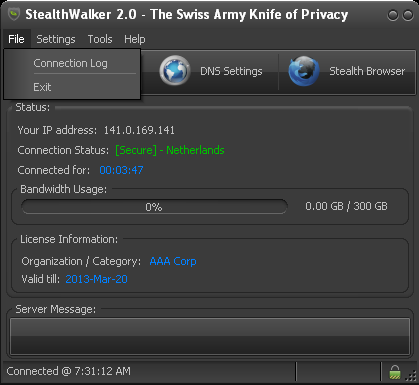
The menu item provides a log of various details about your VPN connection.
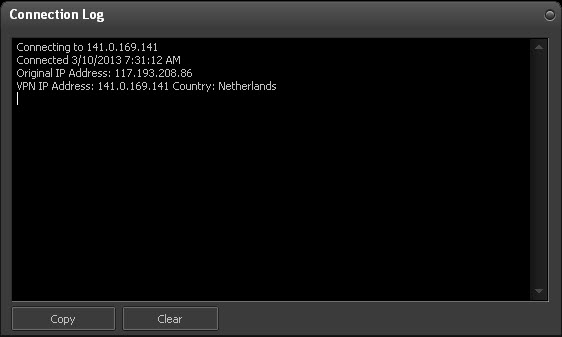
There are two buttons in this window. The button copies all this information to the clipboard and the button removes them from the window.
The menu item quits StealthWalker.
Settings
The menu has three menu items - , and .
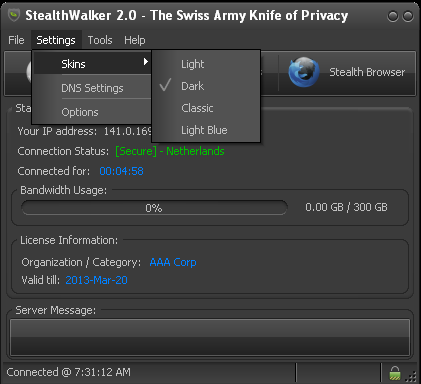
The menu item allows you to change the appearance of the StealthWalker application. The default is "Light Blue" which has blue/white appearance and the other options available are "Light", "Dark" and "Classic".
The menu item brings up the DNS Settings box. This is the same box that is accessed through the DNS Settings button on the main panel. For information on this box, please refer to the section on DNS Settings.
The menu item displays the options window where you can set your preferences for the StealthWalker software.
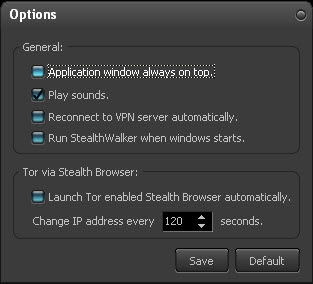
The options available are:
- to have the StealthWalker window on top of every other window,
- to play sounds on various events like connecting, disconnecting, etc.,
- to reconnect to the VPN server automatically once the StealthWalker software is launched or disconnected,
- to run StealthWalker when Windows starts,
- to launch StealthBrowser with the built-in Tor client automatically on launching the StealthWalker software,
- to change the IP address of StealthBrowser periodically and also set how frequently you want it changed.
Click on to save your preferences or to revert back to factory settings.
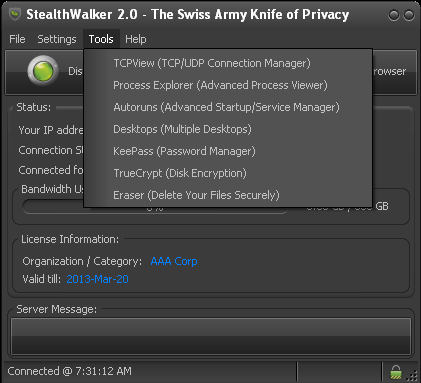
Tools
The menu has a list of various system utilities that are bundled with StealthWalker. These tools have been discussed separately in the "Packaged Tools" section.
Help
The menu provides support information and help for using StealthWalker.
- The provides a link to the StealthWalker user guide on the EEDS website.
- The provides a link to download the PDF guide.
- takes you to the web-based control panel discussed in the next section.
- provides a link to EEDS' Contact page.
- gives the download page link to download updates to the StealthWalker software.
- provides a link to EEDS website.
- displays StealthWalker software information.
System Tray
StealthWalker, when running, has a system tray that provides information and options.
This also provides information on connections, ability to launch tools, etc. and provides notifications when VPN connections are established or closed.
StealthWalker Control Panel Top
The StealthWalker VPN software comes with an extensive, web-based Control Panel access. To go to the Control Panel, click on the option in the menu.
This will take you to the StealthWalker control panel login screen at https://www.digi77.com/software/vpn/user.php through your default web browser.
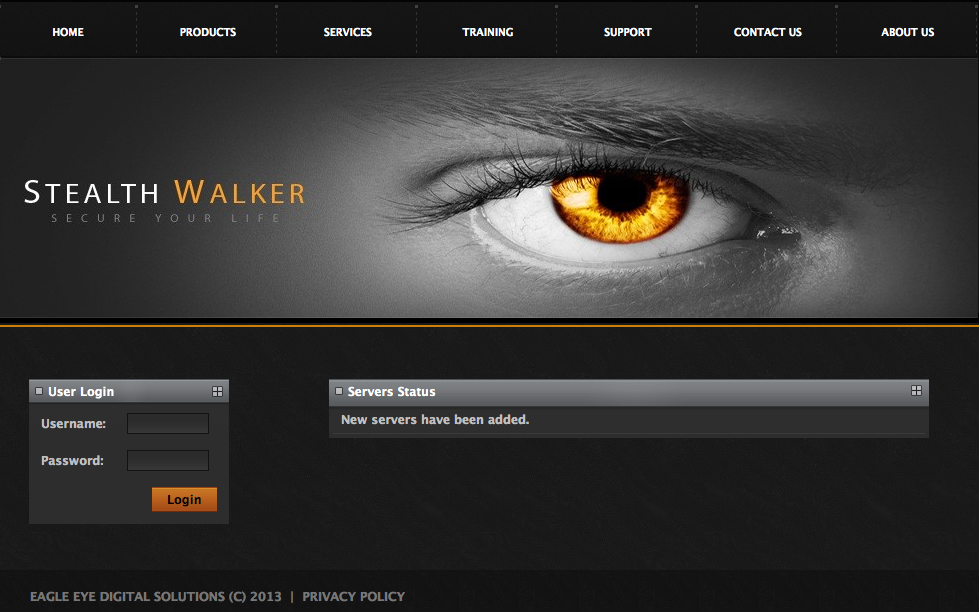
You will need to type in your access credentials in the Username and Password fields and then click on the Login link. If you are an administrator, you will be provided with various administration options. If you are not an administrator, you will only see only one item .
Account Information
Account Information provides you with basic information about your StealthWalker account. If you click on the Account Information link, it will expand to show another link called View Information. The View Information link allows you to view or change your account details.
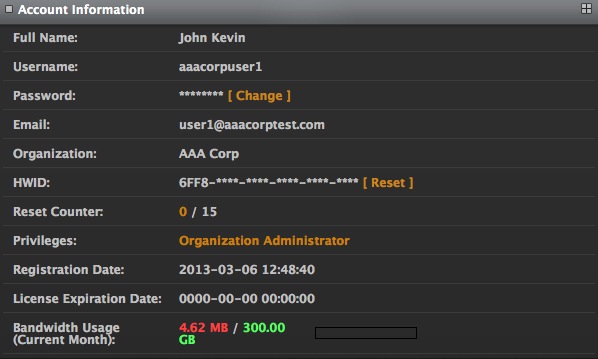
It displays your Full Name, Username, Password (encrypted and hidden), your Email, the Organization to which you have been registered, your computer's hardware ID (HWID), how many times you have reset your hardware ID (Reset Counter), the current Privileges you have on the system, your Registration Date, the date when your license expires (License Expiration Date) and your current month's Bandwidth Usage.
To change your password, click on the Change link. This will take you to the Change Password page where you can type in your new password in the New Password field. Clicking on the Change button will update your password.
If you have switched your computer, for some reason, you can reset your hardware ID so that the StealthWalker software will run from a different computer without deactivating your account. To do this, click on the Reset link next to the HWID field.
Note: You are allowed to reset your hardware ID up to a maximum of 3 times. If you need to change your hardware ID beyond that, you will have to contact your administrator or StealthWalker support.
VPN Users
The VPN Users link expands to show you the following options:
Add VPN User
The Add VPN User link enables you to create new VPN users for your organization. Clicking on the link will show the Add VPN User form on the screen.
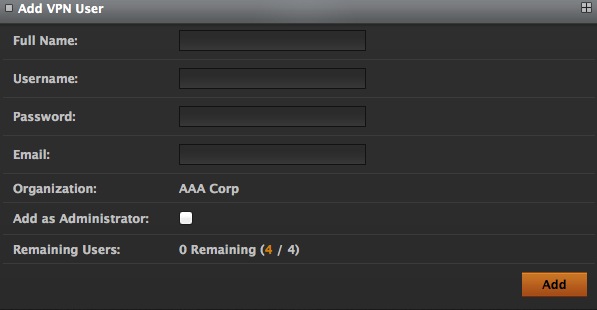
First, type in the Full Name of the user for whom you are creating the account. You can type in a Username, Password and Email in the next three fields. The screen shows the Organization you belong to. If you want to add the user as an Administrator for your organization, check the Add as Administrator box. The screen also shows how many users (Remaining Users) you can create based on the user limit in your organization's StealthWalker license.
Clicking on the Add link will create the user and add them to your organization's list of StealthWalker users.
View VPN Users
The View VPN Users link provides a list of StealthWalker VPN users in your organization.
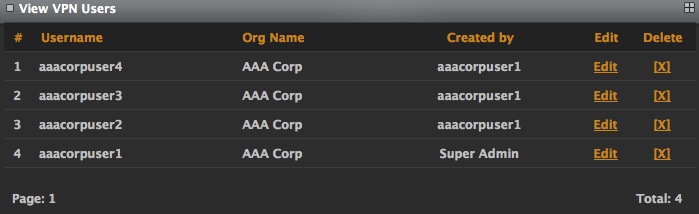
It provides information like their Username, Organization Name and who created the user. It also provides options for editing the user's information using the Edit link and to delete the user from the system using the Delete link. If there are more than 10 users, the information is displayed in multiple pages.
To edit a user's information, click on the Edit link.
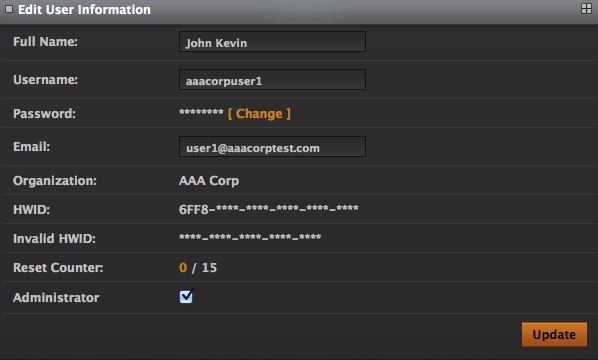
It shows all the fields that were shown in the Account Information link and in addition, also provides the ability to make a user an administrator (by checking the Administrator box) or make an user a regular user (by de-selecting the Administrator box). Clicking on the Update link will update the information.
View Users (Last Login)
This screen provides information on the last time at which a particular user has logged in to the system.
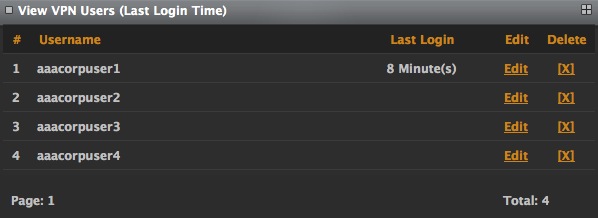
It also provides two options - to edit the user's information using the Edit link and to delete the user from the system using the Delete link. Both of these links lead to the same page as seen in the page.
View VPN Users (Admin Rights)
This list provides only users who have administrative rights on the system.
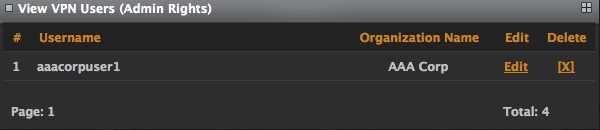
It provides the options to edit or delete the user from the system.
Search
The Search link enables you to search for users based on specific values.
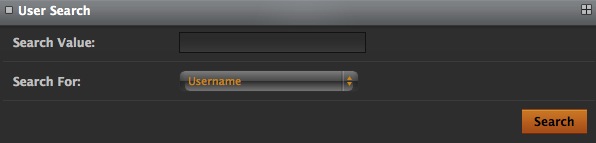
You can search by two fields - Username and Hardware ID. Type the value that you want to search on in the Search Value field, select the field you want to search in the Search For field and click on the link. This will give a list of users that match your search criteria.
VPN Login Logs
This section allows you to look at and search for usage information of the StealthWalker system.
View Login Logs
This section allows you to look at usage logs of the StealthWalker software.
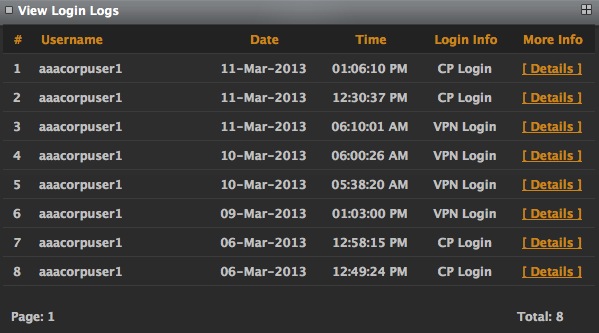
The screen provides information like the Username, Date and Time of the logging in to the StealthWalker VPN software, login information, etc. It also provides a Details link to view more details about their session.
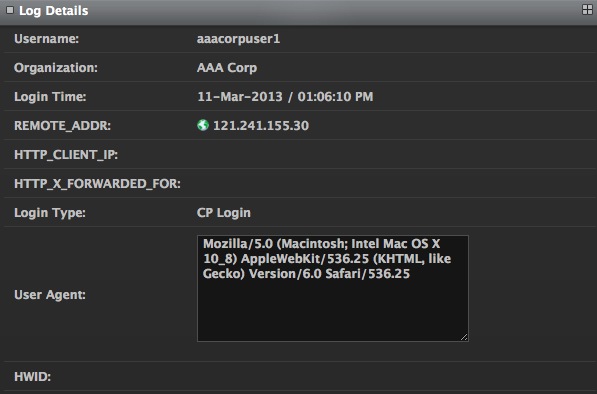
These details include the Username, Organization to which they belong, their last Login Time, IP address from which they logged in (REMOTE_ADDR), the location from which they log in (HTTP_CLIENT_IP), the IP address from which they were forwarded if they are behind a proxy server (HTTP_X_FORWARDED_FOR), the Login Type and what their browser and computer information is (User Agent) and their hardware ID (HWID).
Search
The Search link enables you to search for specific values on various fields.
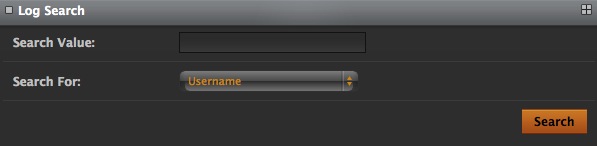
Unlike the earlier Search option, this allows you to search on a lot more fields like Username, REMOTE_ADDR, HTTP_CLIENT_IP, HTTP_X_FORWARDED_FOR, etc.
Logout
You can log out of the Control Panel by clicking on the Logout link.
Packaged Tools Top
StealthWalker comes packaged with various tools that help you with online security and various other system functionalities. You can access these tools from the menu with the exception of StealthBrowser which has its own launcher button in the main interface.

StealthBrowser
StealthBrowser is a secure version of a portable Comodo IceDragon web browser that masks your identity on the Internet. StealthBrowser has a built-in Tor client (www.torproject.org). StealthBrowser provides anonymity on top of the security that StealthWalker provides.
Tor is an online network that provides you anonymity on the Web and allows you to browse for content anonymously.
The StealthWalker software has a special button named as , which launches a secure browser. You can continue browsing the Internet on the secure browser assured that your history, cache and browsing pattern cannot be traced.
When you launch StealthBrowser, you will be assigned a new IP address for your secure browser that is different from your assigned VPN IP address. This IP address may change periodically based the Tor settings on StealthWalker settings window. Surfing using StealthBrowser might seem slower since the Tor network adds another layer of encryption on top of the encrypted tunnel that you already have.
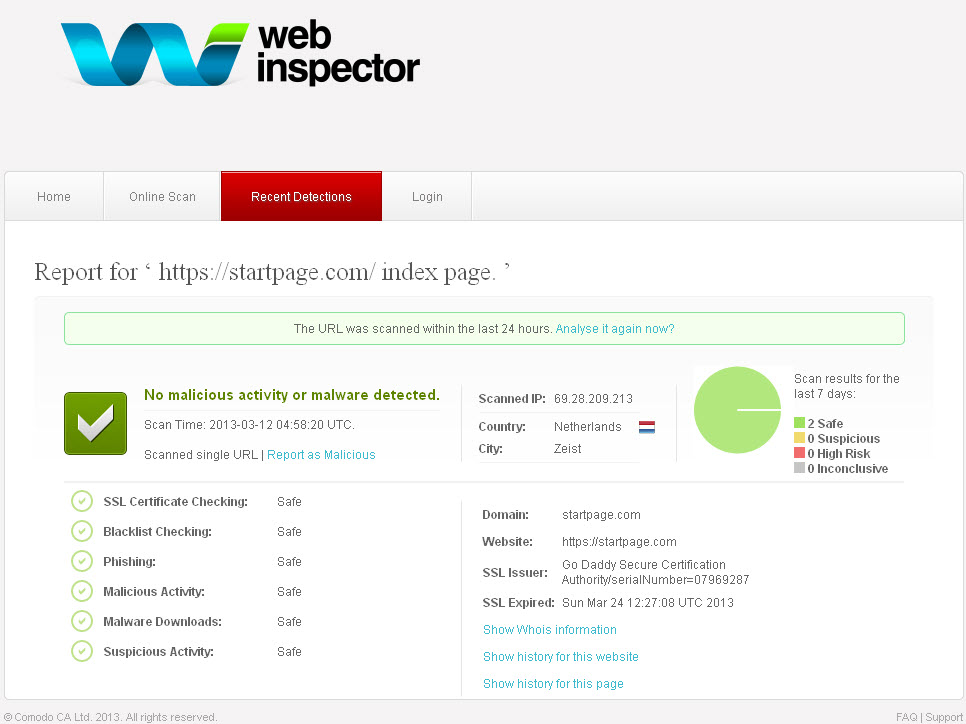
StealthBrowser also includes additional tools that you can use to enhance your privacy, anonymity and security while being online. Notable are the included Comodo WebInspector which scans your network, webpage, etc. for malicious activities, verifies SSL certificates, phishing activities, malwares, blacklisting, etc.
StealthBrowser also includes easy-to-access buttons for enabling or disabling plugins like Flash, Silverlight, Javascript, Java, etc. which can, at times, pose security holes.

Our recommendation is to use your regular browser with VPN enabled for secure browsing like checking emails, viewing or posting to forums, etc. but use StealthBrowser if you want high anonymity on top of the security.
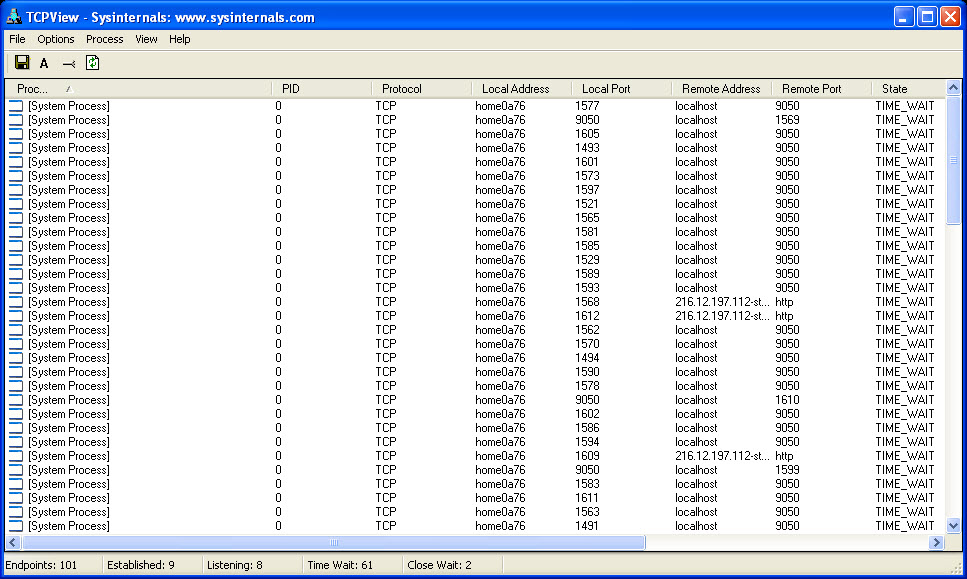
TCPView
TCPView is a Windows program that will show you detailed listings of all TCP and UDP end points on your system, including the local and remote addresses and state of TCP connections. It also allows you to kill a process or application that may have any suspicious connections. On Windows 7, Vista, and XP, TCPView also reports the name of the process that owns the endpoint. TCPView provides a more informative and conveniently presented subset of the Netstat program that ships with Windows.
To know more about TCPView, visit http://technet.microsoft.com/en-us/sysinternals/bb897437.
Process Explorer
Process Explorer is a tool that displays running processes in an intuitive tree format that includes not only process names, but also program icons and other data, such as description, image, and processor time. It also can identify the process for a given application window or look up a process name in Google.
To know more about Process Explorer, visit http://technet.microsoft.com/en-us/sysinternals/bb896653.
Autoruns
This utility, which has the most comprehensive knowledge of auto-starting locations of any startup monitor, shows you what programs are configured to run during system boot up or login, and shows you the entries in the order Windows processes them. These programs include ones in your startup folder, Run, Run Once, and other Registry keys. You can configure Autoruns to show other locations, including Explorer shell extensions, toolbars, browser helper objects, Win logon notifications, auto-start services, and much more.
To know more about Autoruns, visit http://technet.microsoft.com/en-us/sysinternals/bb963902.
Desktops
Desktops is a tool that provides the option of having multiple desktop areas on your Windows computer. It enables you to create more than one desktop (up to four desktops) and switch between them to avoid cluttering of windows on your desktop.
To know more about Desktops, visit http://technet.microsoft.com/en-us/sysinternals/cc817881.
KeePass
KeePass is a free open source password manager, which helps you to manage your passwords in a secure way. You can store all your passwords in one database, which is locked with one master key or a key file. So you only have to remember one single master password or select the key file to unlock the whole database.
To know more about KeePass, visit http://keepass.info.
TrueCrypt
TrueCrypt is a software system for establishing and maintaining an on-the-fly- encrypted volume (data storage device). On-the-fly encryption means that data is automatically encrypted right before it is saved and decrypted right after it is loaded, without any user intervention. No data stored on an encrypted volume can be read (decrypted) without using the correct password/key file(s) or correct encryption keys. Entire file system is encrypted (e.g., file names, folder names, contents of every file, free space, meta data, etc.).
To know more about TrueCrypt, visit http://www.truecrypt.org.
Eraser
Eraser is an advanced security tool for Windows which allows you to completely remove sensitive data from your hard drive by overwriting it several times with carefully selected patterns. Eraser is currently supported under Windows XP (with Service Pack 3), Windows Server 2003 (with Service Pack 2), Windows Vista, Windows Server 2008, Windows 7 and Windows Server 2008 R2.
To know more about Eraser, visit http://eraser.heidi.ie/.


